Threat actors are increasingly focusing their attention on identity-based attack vectors. And there’s one big reason for this. It works.
This blog post dives deep into the evolution of current approaches to authentication and their vulnerabilities and offers a fresh perspective to a wider view of Identity that is required to secure enterprise data, services and resources from the modern attack threats.
Here's what you'll learn:
- How attackers are exploiting current authentication methods to steal credentials and breach your data
- The evolution of authentication approaches
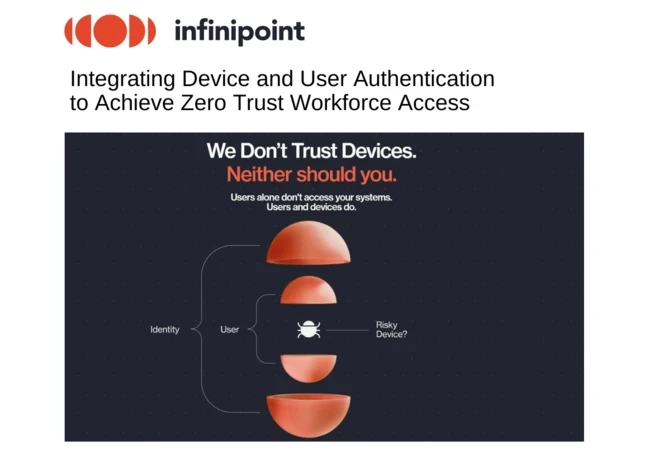
- The move towards Zero Trust Workforce Access
- The key features a Zero Trust Workforce Access solution needs to ensure both security and a smooth user experience







Comments ( 0 )