Have you ever filled out a form online and wondered where that information goes?
Ideally, it travels securely to a database set up by the company you’re submitting it to. But what if a hidden trapdoor existed, waiting to inject malicious code and steal your data? Code injection attacks are a dangerous type of cyber attack that does just that.
By understanding the nature of these attacks developers and security professionals can implement robust defenses to protect themselves against them.
In this article, we'll tell you everything you need to know about code injection, how it works, the different types of code injection attacks and how to prevent them.
What is Code Injection?
Code injection is a cyber attack that exploits a vulnerability in a program to inject malicious code onto a device. This allows hackers to compromise your device and introduce viruses, malware or worms that can prove disastrous.
These attackers can leverage their access to your devices to steal your sensitive information including usernames, passwords and financial information.
By injecting malware onto your device the cybercriminal can gain long-term control of your data and use it to launch further attacks. This could go as far as gaining complete control over your system which allows them to tamper with files.
How Does Code Injection Work?
Code injection preys on weaknesses in how data input is handled. If a program doesn't properly validate or sanitize data, attackers can sneak in malicious code disguised as regular input. The program, tricked into trusting this code, executes it, giving the attacker an access point within the system.
A code injection attack usually follows a similar process:
1. Vulnerability
This is when there is a weakness in the program's handling of user input. This could be due to poor validation or sanitization of data. Validation checks the format of the data. For instance, a username might only allow letters and numbers, while a password might require a minimum length and special characters. If the program doesn't validate the input, an attacker can submit nonsensical data or code that disrupts the program's logic.
Sanitization removes potentially harmful characters from the input. Even if the data format seems valid, it might contain malicious code hidden within seemingly harmless characters. Sanitization processes would identify and remove these threats before they can be executed.
2. Injections
The attacker then sends in malicious code disguised as valid input through a form, search bar, or other input field. They exploit the program's vulnerability by crafting this malicious code to appear like regular user input.
Attackers can encode malicious code using special characters that the program interprets as regular data. Decoding later within the program reveals the true malicious intent.
Some programs allow functionalities within the input field. For example, a search bar that lets you use special symbols for advanced searches. Attackers can misuse these functionalities to inject code that the program tries to interpret as part of the search query.
3. Execution
Execution is when the program interprets the attacker's code as part of its own instructions and executes it. The main three execution methods are string concatenation, database queries and command line execution.
String concatenation is when the program builds a larger string by combining user input with its own code. If the user input contains malicious code, it becomes part of the final string that's executed.
In database queries the user input is used to construct a database query where an attacker can inject malicious code. In some cases, the program might execute user input directly as commands on the system, this is called command line execution, which is especially dangerous as it grants the attacker access to system functionalities.
4. Impact
The attacker's malicious code can perform various actions depending on their goals. The code might extract sensitive information like usernames, passwords, or credit card details and send them back to the attacker.
It can be used to download and install malware onto the device, giving the attacker long-term access for further attacks or it might manipulate files, disrupt system processes, or even cause a complete system crash.
Types of Code Injection
There are multiple types of code injection that each target a specific platform or functionality. The three main types are:
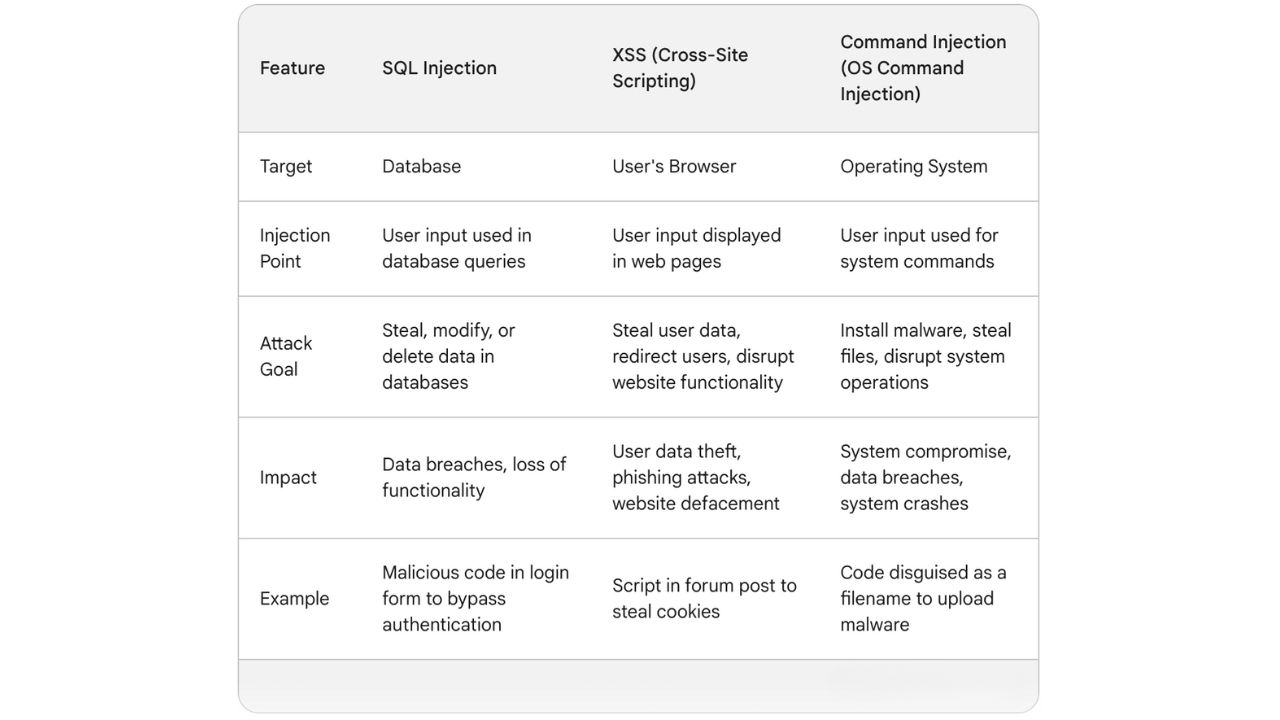
1. SQL Injection
An SQL injection attack injects malicious SQL code into seemingly harmless queries sent to a database. Attackers trick the application into running malicious SQL code instead of the intended queries. This can have severe consequences, allowing attackers to steal sensitive data, tamper with information, or even gain control of the database server.
2. XSS (Cross-Site Scripting)
XSS attacks target web applications by injecting malicious scripts into web pages. These scripts run within the user's browser when they visit the infected page.
In reflected XSS attacks the attacker injects the script into a URL or form, and when the program reflects that data back to the user (like in a search result), the script gets executed in the user's browser.
In stored XSS attacks the attacker injects the script directly into the website's codebase. This script infects every user who visits the compromised page.
3. Command Injection (OS Command Injection)
Command Injection attacks inject code that allows the attacker to execute commands directly on the system's operating system. An attacker might try to inject malicious code disguised as a filename to gain un-authorized access to the system.
How to Prevent Code Injection
Although code injection attacks can wreak havoc by stealing sensitive data, disrupting systems, and compromising entire networks by understanding the vulnerabilities and implementing robust security measures, you can significantly reduce the risk of falling victim to these attacks.
Implement Secure Coding Practices
Validate all user input to ensure it meets expected formats and data types. Reject any input that seems suspicious or doesn't conform to the expected format. Even if the format seems valid, sanitize user input to remove potentially harmful characters that could be malicious code. This might involve techniques like character escaping or filtering based on a whitelist of allowed characters.
Instead of directly embedding user input into database queries, use parameterized queries. These queries use placeholders for user input, which are then filled with the sanitized data separately. This prevents the code from misinterpreting user input as part of the SQL statement.
For complex database operations, consider using stored procedures. These are pre-compiled and secure functions stored on the database server. They reduce the risk of SQL attacks as the code is already defined and validated.
Implement Secure Software Development Practices
Ensure you keep your software up-to-date with the latest security patches, developers often fix vulnerabilities related to code injection in these updates.
In businesses, enforce secure coding standards within your development teams, emphasizing proper input handling and validation techniques to prevent common coding mistakes that lead to vulnerabilities. As well as this, regularly perform security testing, including testing, to identify and address potential vulnerabilities in your applications before attackers exploit them.
Install Additional Software
Install a web application firewall (WAF) to act as the first defence layer of security. WAFs can detect and block malicious traffic, including attempts to inject code into web applications. Also ensure that you implement proper access controls for your databases, restricting access to sensitive data only to authorized users and applications.
Code injection attacks pose a significant threat, but understanding the mechanisms and implementing proper safeguards can significantly bolster your defences. Stay updated on the latest threats, implement regular security testing, and consider using additional security software like WAFs.