
The cybersecurity world was sent into a panic when Sony Pictures Entertainment fell victim to a devastating cyber attack in 2014. The attack sent shockwaves through the entertainment industry, exposing sensitive corporate data, unleashing a trove of internal emails, and even leading to the cancellation of a major motion picture release.
In the ensuing chaos, suspicion swiftly turned to the so-called Lazarus Group, an entity infamous for its audacious ventures into cyber warfare. The group's ruthless disregard for boundaries highlighted the evolving nature of digital threats, leaving Sony Pictures scrambling as it raced to stem the tide of damage and fortify its defences.
What became known as one the biggest cyber attacks in history served as a rallying cry for industries worldwide, sounding the alarm on the necessity of bolstering cybersecurity measures in an era of pervasive digital interconnectivity. It laid bare the harsh realities of modern-day cyber warfare, compelling organisations to confront the looming threat of malicious actors with urgency and vigilance.
This article tells you everything you need to know about Lazarus Group, including who they are, their history of attacks, and how you can defend against them.
Who is Lazarus Group?
Lazarus Group, otherwise known as APT38, is an infamous hacker group believed to be based in the North Korea. It’s known for its sophisticated and highly coordinated cyber attacks targeting governments, financial institutions, and businesses.
Recognised under aliases such as Guardians of Peace, Hidden Cobra, and APT38, Lazurus has been a prominent threat in the cybersecurity landscape since as early as 2009. Although it is not clear who is really behind the group, the US and other governments have linked the group to the government of the DPRK, commonly referred to as North Korea.
This group has left a trail of high-profile cyber incidents, including the infamous Sony Pictures Entertainment hack, the widespread WannaCry ransomware attack, and the Bangladesh Bank heist. Their repertoire extends to consistently targeting South Korean public institutions and critical infrastructure dating back to at least 2011.
Undoubtedly, the modus operandi of the Lazarus Group is marked by a distinctive flair whenever it launches a cyber campaign. Its operations are anchored in three pillars: espionage, sabotage, and financial gain. While the identity of this group has long been a subject of speculation, a significant breakthrough occurred in 2021.
The US Department of Justice indicted North Korean citizens for their involvement in a string of cryptocurrency crimes spanning six years, from 2014 to 2020 and claimed it as part of the Lazarus Group. This development provided a tangible link between the Lazarus Group's activities and the secretive regime in Pyongyang.
However, gaining insight into the inner workings of the Lazarus Group from within North Korea remains a daunting challenge.
The regime’s closed-off nature shields its cyber operations from external scrutiny, making it exceedingly difficult to discern its methods. Nevertheless, defector accounts have provided glimpses into the existence of a covert unit known as the 414 Liaison Office. According to these sources, this clandestine entity serves as the nerve centre for orchestrating the Lazarus Group's disruptive activities, operating under the directive of the North Korean Reconnaissance General Bureau.
Who Does Lazarus Group Target?
Lazarus Group has predominantly targeted South Korea, but its reach extends beyond neighbouring borders. With a track record of cyberattacks not only in South Korea but also in the United States and various other countries, Lazarus Group has garnered international attention for its sophisticated tactics and disruptive operations.
Despite efforts by cybersecurity experts and law enforcement agencies to counter its operations, Lazarus Group continues to pose a significant threat to organisations and governments worldwide. The group's ability to adapt its techniques and evade detection underscores the ongoing challenges in combating cybercrime globally.
As authorities intensify their efforts to disrupt Lazarus Group's operations and hold its members accountable, cybersecurity professionals emphasise the importance of robust defence measures, proactive threat intelligence sharing, and international cooperation to mitigate the impact of cyber threats emanating from groups like Lazarus.
A History of Lazurus Group
Lazarus Group has left an indelible mark on the records of cyber warfare since its inception. The earliest known attack attributed to this shadowy collective is codenamed Operation Troy, a nefarious campaign that unfolded between 2009 and 2012.
The Lazarus Group's mode of attack has become increasingly refined since then, marked by a trifecta of espionage, sabotage, and financial gain. Notorious incidents such as the WannaCry ransomware attack in 2017, and the cyber heist targeting Bangladesh Bank in 2016 showcased the group's evolving tactics and relentless pursuit of its objectives.
Despite global efforts to dismantle their operations and expose their identities, the Lazarus Group continues to pose a formidable threat to cybersecurity on a global scale.
As nations and organizations bolster their defences and collaborate to combat cybercrime, the Lazarus Group's saga stands as a reminder of the ever-present dangers lurking in the digital world.
History of Lazurus Group Cyber Attacks
1. Operation Troy (DDoS South Korean) - Espionage
The emergence of the Lazarus Group onto the cybersecurity scene in 2013 drew widespread attention with the publication of two reports linking them to targeted campaigns in South Korea. Among their earliest documented activities was "Operation Troy," a cyber espionage initiative that unfolded between 2009 and 2012. During this period, the group leveraged malicious tools like Mydoom and Dozer to orchestrate a sizable but relatively rudimentary distributed denial-of-service (DDoS) against a swath of US and South Korean websites.
The repercussions of these attacks were felt across the digital landscape, disrupting operations on approximately a dozen websites while leaving an indelible mark by modifying the Master Boot Record (MBR) with the phrase "Memory of Independence Day." These brazen actions not only served as a stark reminder of the vulnerabilities inherent in the digital realm but also signalled the inception of Lazarus Group's disruptive operations.
This incursion marked the beginning of a prolonged and multifaceted cyber campaign that would put Lazarus Group into the spotlight as a formidable threat actor on the global stage. Over the ensuing years, their tactics would evolve in sophistication and scope, encompassing a wide range of targets and methodologies. Yet, the memory of their inaugural attacks in Operation Troy remains a chilling reminder of the enduring impact and enduring threat posed by this shadowy collective.
2. Sony Breach - Sabotage
In November 2014, the cyber world was rocked by a Reddit post signalling a devastating breach at Sony Pictures, attributed to a group calling themselves the "Guardians of Peace." The fallout was nothing short of catastrophic: stolen data flooded the internet, exposing unreleased blockbuster films, internal correspondence, and sensitive employee information encompassing over 4,000 individuals.
In a chilling display of their capabilities, the hackers unearthed a treasure trove of unreleased films, scripts, and strategic plans, casting a shadow of uncertainty over Sony's future endeavours. Amidst the chaos, whispers of motive swirled, with some speculating that the attack was a retaliatory strike linked to the controversial film "The Interview," which depicted North Korean leader Kim Jong Un in an unflattering light.
The repercussions were swift and severe. Sony Pictures found itself embroiled in a reputational crisis, compounded by the cancellation of "The Interview's" theatrical release—a move widely seen as capitulation to the hackers' demands. Yet, amidst the chaos and speculation, questions lingered over the true identity of the perpetrators. While initial finger-pointing pointed towards North Korean hackers, the sheer sophistication of the attack prompted theories of Russian involvement, potentially acting as proxies for Pyongyang's clandestine objectives.
3. Bangladesh Bank Cyber Heist - Financial Gain
It was February 4th, 2016, and what initially seemed like a routine glitching printer was about to unveil a far-reaching cyber heist. As the Bangladeshi government grappled with the unexpected disruption, little did they know that the sinister hand of the Lazarus Group had been at play within the bank's networks for over a year.
In January 2015, several Bangladesh Bank employees received a seemingly harmless email from an individual identifying as Rasel Ahlam, a job seeker. The email courteously requested the recipients to download Rasel's CV and cover letter from a provided website link. However, investigations by the FBI later revealed that Rasel Ahlam was a fabricated identity used by the Lazarus Group. Regrettably, at least one bank employee fell victim to the deception, unwittingly downloading the documents and inadvertently infecting their system with concealed viruses.
In a meticulously coordinated operation that bore all the hallmarks of their trademark sophistication, the hackers manoeuvred to authorise a series of fraudulent transactions. Through a combination of social engineering tactics and compromised credentials, they gained access to the Bangladesh Bank's SWIFT network, a global messaging system used by financial institutions for secure communication and transactions.
When the bank's staff rebooted the printer, they received alarming messages from the Federal Reserve Bank in New York - the "Fed" - where Bangladesh maintained a US-dollar account. The Fed had received instructions, apparently from Bangladesh Bank, to drain the entire account, which amounted to close to a billion dollars.
Desperate for clarification, the Bangladeshis attempted to contact the Fed, but the hackers' meticulous timing thwarted their efforts. The hack began around 20:00 Bangladesh time on Thursday, February 4th. However, it was Thursday morning in New York, giving the Fed ample time to (unwittingly) comply with the hackers' instructions while Bangladesh slept.
What started as a malfunctioning printer escalated into a nightmare scenario. In the world of modern banking, technical glitches are commonplace, and the staff at Bangladesh Bank initially treated it as such - just another day, another tech headache. But this printer was no ordinary device, and Bangladesh Bank was no ordinary institution.
As the country's central bank, Bangladesh Bank held the responsibility of overseeing the nation's precious currency reserves, a task of utmost importance in a country where millions struggled with poverty. Located within a highly secure room on the 10th floor of the bank's main office in Dhaka, the capital, the printer played a crucial role. Its function was to print records of the multi-million-dollar transfers coursing in and out of the bank, making it a keystone in the nation's financial infrastructure.
The cyberattack on Bangladesh Bank resulted in the theft of approximately $81 million. Some of the stolen funds were traced to casinos in Macau, highlighting the international reach and complexity of the cyber heist orchestrated by the Lazarus Group.
Despite desperate attempts to halt the unauthorised transactions and mitigate the damage, the hackers' cunningly orchestrated scheme had already inflicted irreparable harm. The breach, masterminded by the elusive Lazarus Group, had shattered the illusion of impenetrability surrounding one of the nation's most vital financial institutions.
Lazarus Group Attack Characteristics
Understanding how cybercriminal organisations work is critical as cybersecurity defences continue to evolve. In a comprehensive report, Peter Kalnai examined the Lazarus toolset, illuminating the modus operandi of one of the most formidable cybercrime syndicates in operation today.
According to Kalnai, at the core of Lazarus malware lies its intricate multi-stage architecture. The attack typically starts from a console application that is proficient in receiving parameters and initialising Windows APIs. Following the initial stage, the attack progresses through a complex process, utilising an encryption method similar to RC4 called Spritz.
This adds multiple layers of complexity, making detection more challenging and enhancing the sophistication of the cyber attack.
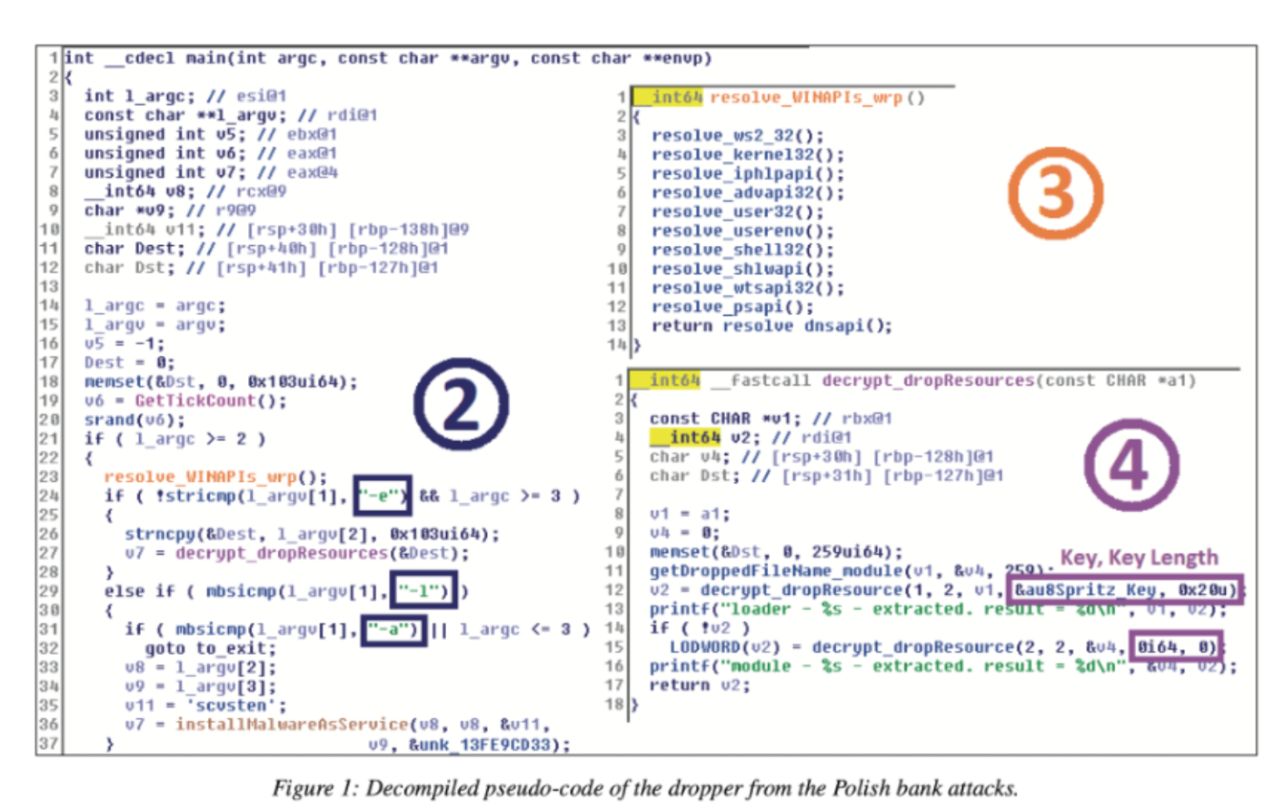
The versatility of Lazarus malware extends to its use of relatively straightforward TCP backdoors, which serve as a gateway for a wide array of commands. These commands, systematically indexed by consecutive integers, provide attackers with a wealth of options, ranging from command-line executions to system manipulation.

These tactics highlight how sophisticated Lazarus operations are, showing the group's ability to adapt and navigate complex network environments. By using various formatting techniques, Lazarus actors can avoid detection and hide their malicious activities, making it difficult for cybersecurity defenders to counter them.
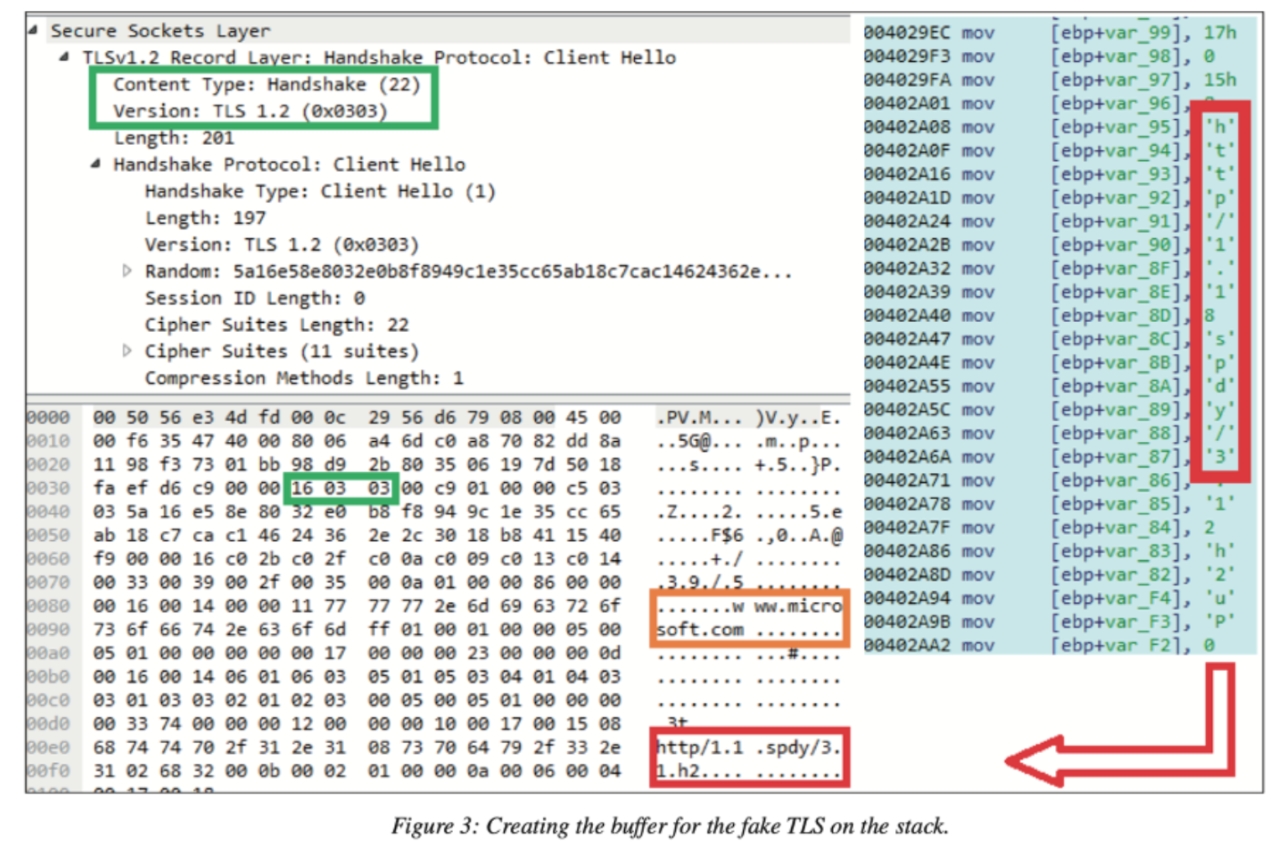
Similarly, as per Kalnai’s report, the group has employed masquerading techniques. Here, Lazarus malware pretends to be genuine TLS protocol traffic. By hiding malicious activities within fake TLS packets, Lazarus attackers make it hard for cybersecurity defenders to detect and address threats. Of particular interest is the deliberate inclusion of popular websites like naver.com, baidu.com, and vk.com in these fake packets. This suggests a deliberate strategy to target victims across various regions and industries.
Defending Against Lazarus
Understanding the Lazarus toolset not only helps decipher technical intricacies but also provides insights into the psychology of cybercriminals. By unravelling their motives, objectives, and operational methodologies, defenders gain a deeper understanding of this evolving threat.
Moreover, this understanding enables organisations to anticipate and counteract the tactics employed by malicious actors proactively. It empowers security and IT professionals to fortify their defences, implement robust security measures, and stay one step ahead of potential breaches.
This involves ensuring that every corner of the network infrastructure is secure and resilient against various types of attacks. Security professionals should continuously update their knowledge and skills to provide effective solutions to evolving cyber threats.
Here's a list of possible solutions to mitigate threats posed by Lazarus Group:
- DDoS Defence. Implementing robust measures to counter Distributed Denial of Service (DDoS) attacks, a preferred strategy of the Lazarus Group, enables organisations to identify and mitigate these assaults, thereby protecting against disruptions and data breaches.
- Protection of Assets. Safeguarding vital digital assets spanning various industries is imperative, particularly in light of their targeting of financial institutions, banks, casinos, cryptocurrency exchanges, and SWIFT system endpoints.
- Ransom Mitigation. Strong security protocols assist organisations in avoiding ransom payments by thwarting attacks orchestrated by malicious entities like the Lazarus Group.
- Threat Intelligence. Harnessing threat intelligence capabilities, thus empowering organisations to promptly detect and address threats emanating from entities such as Lazarus, providing defence against DDoS attacks, ransomware incidents, and other cyber threats.












