
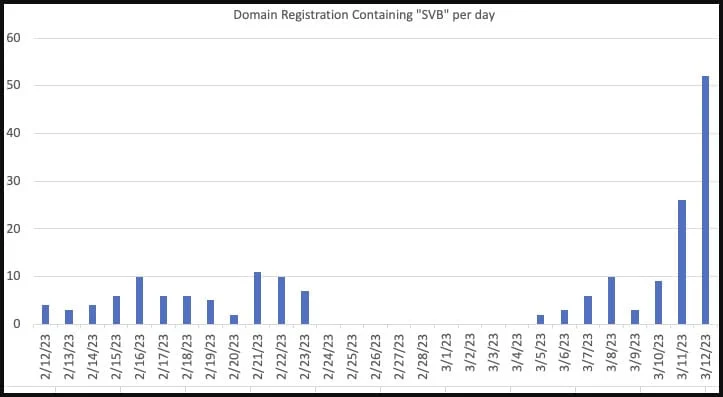
In the aftermath of Silicon Valley Bank’s collapse, threat actors have begun exploiting the financial crisis to launch sophisticated cyber attacks against SVB clients.
Silicon Valley Bank (SVB) was the 16th largest in the US but collapsed after investors triggered a liquidity run. This left its customers – mostly from the technology, private equity, venture capital, and life-science sectors – in a panic until their deposits were guaranteed by the FDIC.
According to security researcher Dr Johannes Ullrich, hackers, scammers and fraudsters have registered a number of dubious domains imitating SVB as part of large-scale phishing campaigns to exploit this panic by targeting the bank's former clients to steal personal information.
According to Ullrich, svbbailout[.]com, svbclaim[.]com, svbcollapse[.]com svbdeposits[.]com, svbhelp[.]com and svblawsuit[.]com are among some of the suspicious URLs related to SVB’s collapse.
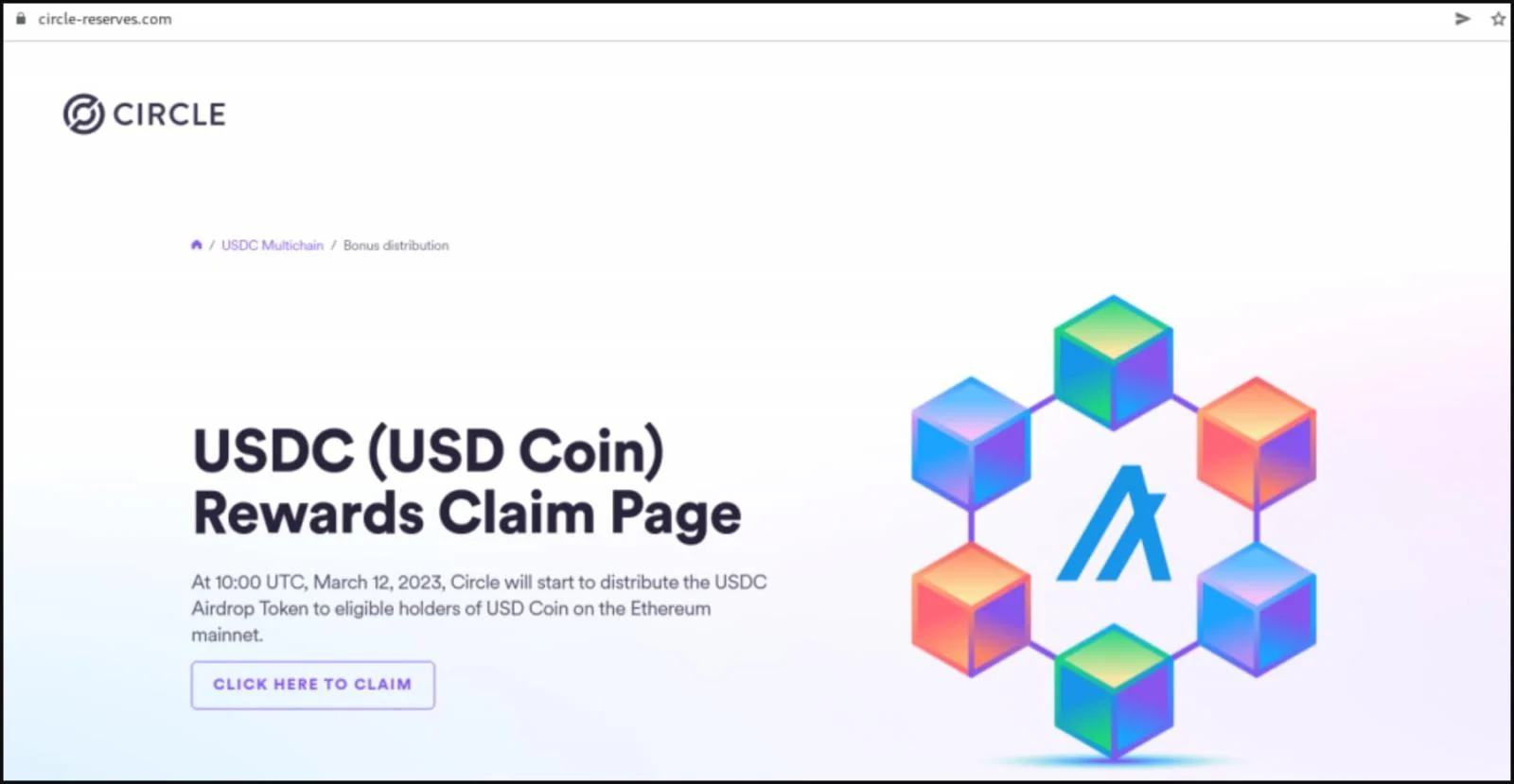
Many of these sites were registered on the day of SVB’s collapse on March 10, and are already hosting cryptocurrency scams. They tell customers that the bank is distributing USDC as part of a "payback" program.
"Silicon Valley Bank is actively distributing USDC as part of the SVB USDC payback program to eligible USDC holders. USDC payouts can only be claimed once per wallet," claims the cryptocurrency scam.
Clicking on the site's 'Click here to claim' button brings up a QR code that, when scanned, attempts to compromise Metamask, Exodus, and the Trust Wallet crypto wallets.
As well as registering suspicious domains, researchers also warn that scammers might attempt to contact former clients of SVB to offer them a support package, legal services, loans or other fake services related to the bank’s collapse.
“Threat actors can leverage phishing emails which could contain new banking wire information, instructing an employee to make changes to benefit the threat actor in this scenario for financial gain,” said James Liolios, Threat Intelligence Researcher at Artic Wolf.
“Threat actors may also target employees’ social media accounts, such as LinkedIn, where they can identify individuals working at startups or other affected organizations,” Mr Liolios added.
A new wave of attacks
As the dust settles in the wake of SVB’s collapse, several companies associated with the bank are faced with financial turmoil – and threat actors are already jumping on the opportunity to exploit this.
Peer-to-peer payments company Circle, which manages the popular stablecoin USDC, has a cash reserve of $3.3 billion in SVB. The bank’s downfall has created uncertainty among USDC coin-holders, despite the firm’s continued assurance of USDC’S liquidity.
This uncertainty has led to the creation of a wave of new cryptocurrency scam sites with the sole purpose of stealing visitors' wallets, digital assets or personal details.
Researchers also note threat actors are mimicking SVB competitors in a bid to trick former SVB clients wishing to transfer their assets to another bank.
To read more about cyber attacks, visit our dedicated Business Continuity Page.
“We have seen domains mimicking Revolut, a British-Lithuanian financial services company, including customer-revolut[.]com, logon-revolut[.]com, and revolutbank[.]net,” said Ashley Allocca, intelligence analyst at Flashpoint.
“There are many companies taking rapid action to update their payment information away from SVB, which presents a prime opportunity for cybercriminals to capitalize on this crisis situation, Ms Allocca said.
Financial bust, cybercrime boom
When the 2008 financial crisis spread from the US to other parts of the world, the economic downturn led to an unprecedented surge in phishing campaigns that sought to exploit customer confusion resulting from the banking crisis.
With SVB’s collapse potentially marking the beginning of a new financial crisis, cybersecurity experts warn customers to remain vigilant as the rate of attacks soars.
The risk of a cyberattack given the recent collapses of SVB, Credit Suisse, Signature has dramatically increased. Organisations need to prepare themselves for heightened levels of … #Cyber #CyberAttacks #Ransomware #Phishing #NetworkIntrusion #Spam #DDOS #Social
— Conor Coughlan (@Capital_FinServ) March 20, 2023
“Given SVB’s breadth of exposure across the startup ecosystem, we should expect to see many finance teams receiving an unusually high number of updates about new banking relationships and wire instructions,” Sounil Yu, CISO of JupiterOne said.
“The SVB situation creates a “tremendous opportunity” for attackers to launch fraudulent vendor email compromise (VEC) and business email compromise (BEC) attacks. They’ll try to convince finance teams to switch banking details over to an attacker-controlled account.
Attackers are likely to indiscriminately impersonate vendors regardless of whether the vendor previously banked with SVB or not,” Mr Yu added.
It’s likely that the fallout from Signature Bank’s failure will lead to a new wave of cyber threats for the enterprise landscape.
Financially motivated threat actors will act opportunistically. They’ll use the same low-level initial access techniques like phishing to prey upon those most impacted by the failure as was used in 2008.












