
The Rhysida ransomware group has threatened to leak data belonging to the Royal Family after a cyber attack on King Edward VII Hospital in central London.
The hospital, which has treated royals such as the Princess of Wales and Prince Philip in recent years, was allegedly breached by the gang last week, giving them access to a host of sensitive data including including copies of X-rays, medical reports, prescriptions and registration forms.
In a dark web post announcing the attack last week, Rhysida posted images of the medical records and records supposedly in its possession. Like previous Rhysida attacks, the group is offering this stolen data for sale, with a price set at around £300,000 in Bitcoin. The fact it is selling the data publicly suggests King Edward VII Hospital declined to pay a ransom.
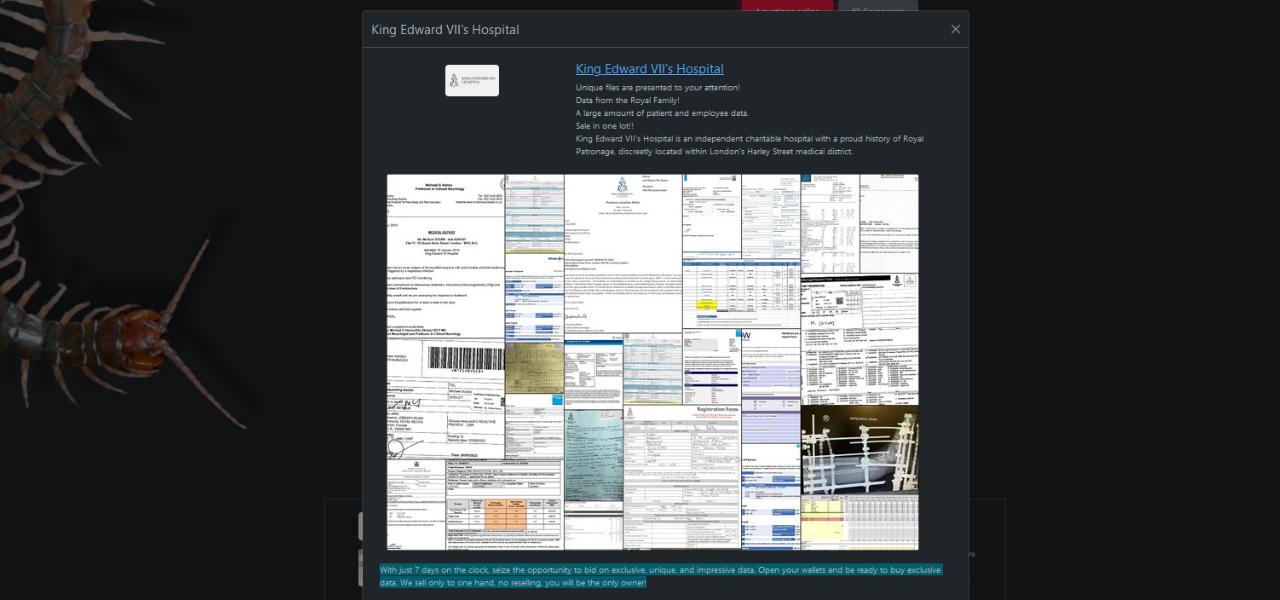
"Unique files are presented to your attention! Data from the Royal Family! A large amount of patient and employee data” reads the Rhysida group’s dark web post.
The hacker group said it would release all of the data publicly on Tuesday, December 5 unless there is a buyer for the data.
The cyber attack has prompted immediate action from the UK's intelligence agencies, with GCHQ and the police each launching an investigation into the hacking group.
A spokesperson for the National Cyber Security Centre (NCSC) said the agency was "engaging with King Edward VII's Hospital to understand the impact."
‘Limited amount of patient information’ Copied
The royal family’s data is reportedly subject to particularly strict cyber security controls and any organisations that hold it cannot do so without taking extensive additional precautions to safeguard it.
It is not known whether royal medical data was stored at the King Edward VII hospital, or if that data was accessed by the Rhysida gang.
But it has maintained close links to the royal family over the past 120 years, providing care to Prince Philip, King Charles III, the Duchess of York, the Princess of Wales and the late Queen Elizabeth II, among others.
In a statement, the hospital confirmed that it was subject to a data breach, but assured that most data was limited to its systems and only a “small amount of data” was copied from its systems.
“We recently experienced an IT security incident involving temporary, unauthorised access to our systems. We took immediate steps to mitigate the incident’s impact and continued to offer patient care and services, largely as normal, said a spokesperson from the hospital.
“We also launched a comprehensive investigation, which confirmed that a small amount of data was copied from part of our IT system. While this was primarily benign hospital systems data, a limited amount of patient information was copied, and we are notifying a small subset of our patient database about this.”
“The vast majority of patients are not affected by this in any way, and we offer our apologies for any concern this incident may cause,” they added.
Who is the Rhysida Ransomware Gang?
Deriving its name from a species of millipede, the Rhysida Ransomware gang was first discovered in May when it launched a series of attacks on the Chilean Army, along with multiple global organisations across public and private sectors around the world.

The Gang has been active since May 2023 and has so far claimed the compromise of 60 victims according to their victim name-and-shame blog. Its most notable attacks include the unfolding cyber attack on the British Library and the breach at the University of West Scotland earlier this year.
Rhysida was first discovered in May when it launched a series of attacks on the Chilean Army, along with multiple global organisations across public and private sectors around the world.
The gang has targeted organizations in multiple industries, including the education, healthcare, manufacturing, information technology, and government sectors. The victims of the group are “targets of opportunity.”
Last week, the FBI and CISA published a joint Cybersecurity Advisory (CSA) to warn of Rhysida ransomware attacks. The advisory is part of the ongoing #StopRansomware effort, sharing information about tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) associated with ransomware groups.
The report includes IOCs and TTPs found during investigations into the group from as recently as September 2023.
“Threat actors leveraging Rhysida ransomware are known to impact “targets of opportunity,” including victims in the education, healthcare, manufacturing, information technology, and government sectors. Open-source reporting details similarities between Vice Society activity and the actors observed deploying Rhysida ransomware.” reads the advisory.
“Additionally, open source reporting] has confirmed observed instances of Rhysida actors operating in a ransomware-as-a-service (RaaS) capacity, where ransomware tools and infrastructure are leased out in a profit-sharing model. Any ransoms paid are then split between the group and the affiliates.”












