
A British hacker has confessed his involvement in the 2020 Twitter attack that saw the accounts of Bill Gates, Joe Biden and Elon Musk hijacked to promote a crypto scam.
Joseph James O’Connor, known online as PlugWalkJoe, could face up to 70 years in prison after being extradited from Spain last month and pleading guilty to hacking charges he faced in a court appearance in New York.
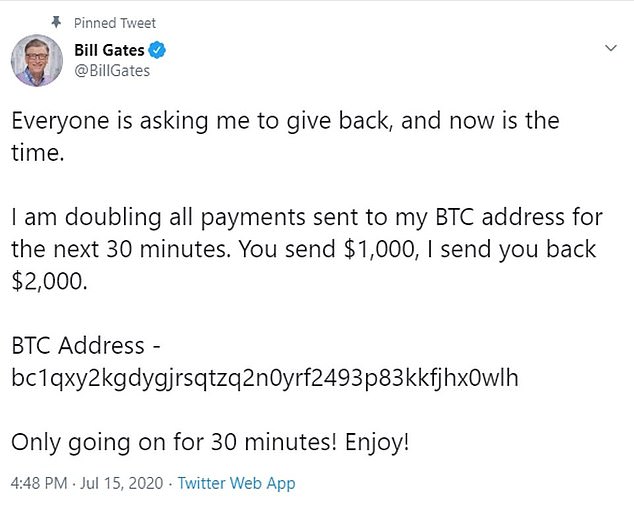
O’Connor was one of four programmers charged with hacking into Twitter in 2020 and accessing the accounts belonging to high-profile individuals and major companies to promote a crypto scheme where they promised to double the Bitcoin sent to their accounts.
“I am doubling all payments sent to my BTC address for the next 30 minutes, the hackers wrote in a scam posted to Bill Gates's Twitter account. You send $1,000, I send you back $2,000,”
Twitter confirmed 130 accounts were targeted as part of the scam, describing the incident as a “coordinated social engineering attack,” whereby the hackers deceived Twitter staff to gain access to “internal systems and tools.”
It was forced to temporarily block all Tweets from verified accounts locked all compromised accounts. O’Connor and his co-conspirators were able to steal more than $794,000 of cryptocurrency from the scam.
Kenneth A Polite Jr, an assistant attorney general in the US justice department’s criminal division said that O’Connor’s actions were “flagrant and malicious” and his conduct “impacted multiple people’s lives”
“Like many criminal actors, O’Connor tried to stay anonymous by using a computer to hide behind stealth accounts and aliases from outside the United States," Polite Jr said.
"But this [guilty] plea shows that our investigators and prosecutors will identify, locate, and bring to justice such criminals to ensure they face the consequences for their crimes.”
SIM swap attack
O’Connor was charged by the U.S. Attorney’s Office Southern District of New York (SDNY) charged with conspiracy to commit wire fraud, conspiracy to commit money laundering, and the intentional access of a protected computer.
He also pled guilty to his role in SIM-swapping attacks targeting high-profile executives in the cryptocurrency industry, which resulted in the theft of $794,000 in digital assets.
“O’Connor used his sophisticated technological abilities for malicious purposes – conducting a complex SIM swap attack to steal large amounts of cryptocurrency, hacking Twitter, conducting computer intrusions to take over social media accounts, and even cyberstalking two victims, including a minor victim,” the SDNY said in a statement.
"O'Connor's guilty plea today is a testament to the importance of law enforcement cooperation, and I thank our law enforcement partners for helping to bring to justice those who victimize others through cyber-attacks."
Despite multi-factor authentication being enabled on many of the accounts, the attackers managed to override scam warning responses, including from Binance CEO Changpeng Zhao, and amassed approximately.
While the SDNY declined to name the company, only stating that it “provided wallet infrastructure and related software to cryptocurrency”, there have been numerous cases of targeted crypto companies using this same technique, including BlockFi.
A nest for cybercrime
This is not the first time high-profile Twitter users have had their accounts infiltrated by hackers. In 2019, two former employees were convicted of espionage after allegedly stealing the account information of numerous users for the government of Saudi Arabia.
Meanwhile, in November 2021, the login information for over five million accounts on the blue bird app was leaked online.
Ireland’s Data Protection Commission (DPC), who investigated the attack, said Twitter’s handling of data, “raised queries in relation to GDPR compliance,” after it was revealed the leaked data had come from a bug in the social media giant’s system that allowed users to identify any Twitter account through an email address or phone number.
The bug was only discovered when a user enrolled in Twitter’s “bug bounty” scheme – which rewards researchers who identify security flaws – notified the social media giant of the flaw.

The Cyber Security & Cloud Expo is the leading event for Zero Trust, Threat Detection & Response, Training, Talent & Culture, Identity & Access Management, Application Security, and Data Security.
Taking place on 17-18 May 2023 at the Santa Clara Convention Center, this is a technology event and conference for ambitious enterprise technology professionals seeking to explore the latest innovations, implementations and strategies to drive businesses forward.
Don’t miss the opportunity to explore this innovative technology and its impact on a range of industries including, manufacturing, transport, supply chain, government, legal sectors and financial services energy, utilities, insurance, healthcare, retail and many more.
Stay ahead of the curve and REGISTER NOW!












